Background
Driven by business benefits from richer real-time information sharing, analysis, and responses, the integration of IT and OT is a well-established trend, however operational technology (OT) security is still often overlooked. Many organizations are shifting towards the Zero Trust security model to strengthen their respective network security and improve cyber resilience across industries.
Zero Trust is a shift from perimeter-based defenses to a security architecture that does not implicitly trust all subjects and continuously validates every stage of digital interaction. The benefit of the Zero Trust model is it creates a far more secure environment that protects against unauthorized access to sensitive data and digital assets. In addition to improved security, the Zero Trust model can also provide comprehensive visibility into network activity and identify potential threats, improve monitoring and alerting; improve the risk of insider threats, streamline security policy creation, and increased agility of resource usage and access.
Requirements
A global manufacturing company had several production plants and required a solution that addressed network-based attacks and industrial operations could be provided with complete visibility, security, and control over their OT networks. They had a complex network infrastructure that included legacy systems, and they needed a solution to secure their OT environment from cyber threats while maintaining their existing infrastructure.
The company turned to a system integrator and Lanner for a rugged cybersecurity appliance to actively secure the industrial environment. The hardware appliance must be sufficiently robust and powerful and have the following functionalities:
- Industrial-grade IEC Certification – Critical infrastructure environments can be harsh, with unexpected ambient temperature fluctuations, shocks, and vibrations, or other external factors. Therefore, deployments in these environments require IEC-61850-3/IEEE 1613 certifications for withstanding these external environmental impacts.
- Wide Operating Temperature – Given the extreme temperature in a critical infrastructure environment, the appliance must be able to operate at a wide temperature range.
- Multi-layer Hardware Security – An onboard TPM for secure crypto-processing and tamper resistance at the hardware level.
- Advanced LAN Bypass – To ensure operations network resiliency, fault-tolerant LAN traffic is essential in ICS communication in case a failure occurs.
- Rich I/O Connectivity Configurations – Various LAN port configurations, including GbE LAN and SFP fiber, serial port connectivity, and wireless connectivity to communicate with PLC (Programmable Logic Controllers) RTU, HMI, and SCADA, to maintain a high level of security.
- Low Power Consumption – The hardware appliance must be low power consumption and optimize power usage during ICS operations. In addition to dual power inputs to offer even high stability in OT domains.
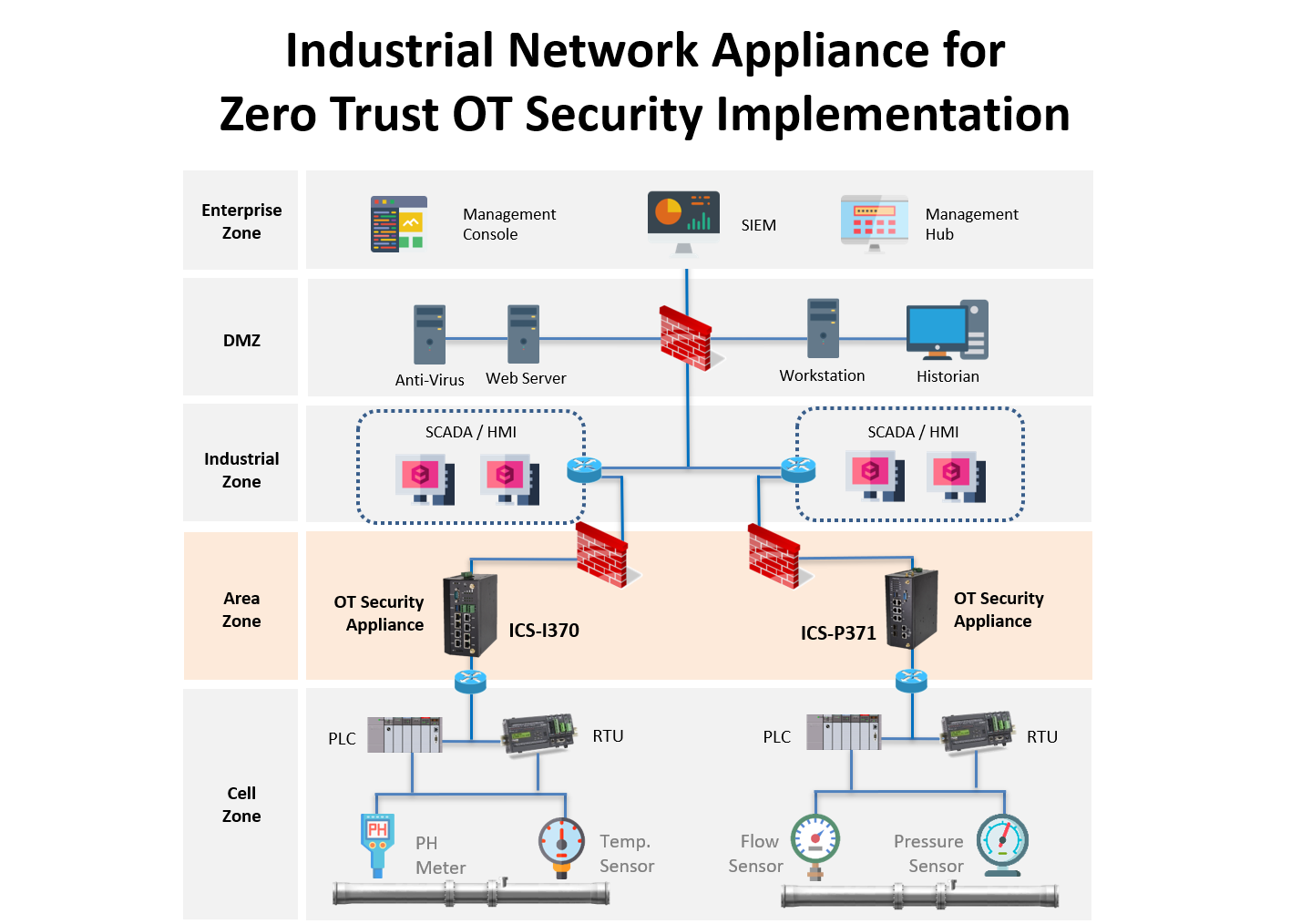
Solution
The benefits of a Zero Trust model for OT cybersecurity are significant, and implementing a Zero Trust OT Security approach through the network appliance, provided the company with a robust security solution that met their needs. The platform's security features provided a strong foundation for securing their network, while the Zero Trust approach helped to mitigate the risks of cyberattacks by ensuring constant verification and authentication of devices and users.
Lanner’s ICS-P371, powered by the Intel® AtomTM X6211E/X6413E/X6425E (formerly Elkhart Lake) CPU for enhanced IoT platform and high processing performance, is designed to protect communication in both IT and OT domains. The next-generation industrial cybersecurity gateway was strengthened with multiple hardware security features including LAN bypass technology, and TPM, in addition to being compliant with IEC 61850-3 and IEEE 1613 to withstand harsh environments and operate in a wide temperature range. All the hardware design assures that the security gateway ICS-P371 will never have downtime while operating in hazardous surroundings such as the OT environment.
ICS-I370 is a compact fanless industrial cyber security appliance with Intel® Atom™ E3900 CPU (Apollo Lake). Deployed in remote, unmanned, and harsh environments, ICS-I370 supports rich LAN ports with advanced Gen3 LAN bypass, SFP, and extended operating temperature from -40 ºC to 70 ºC. It also boosts a flexible design with versatile mounting options (wall mount or DIN-rail), onboard TPM, wireless connectivity options, and front access I/O ports, making it perfect for performing OT cybersecurity measures at critical infrastructures such as oil refineries, substations, power plants, and manufacturing factories.








