In the past few years, electrical substations have become a primary target for cyberattacks. In fact, it is believed that power facilities are targets for modern cyber warfare.
Cybercriminals look for components and services within electrical substations that can be easily modified, degraded, or even disabled. When cybercriminals are successful, entire populations dependent on electricity, including government agencies, military, and other utilities, are left without their major power source.
The Power Substation Cyber Attack That Shook the World
In December 2015, a power grid in the region of Ukraine went down for six hours. According to Wired’s full report on Ukraine's power grid hack, the power outage was due to a cyberattack that caused the devices that route power and change voltages to disconnect from the main grid.
Although Ukraine’s power grid network was properly segmented from the control center networks using firewalls, the remote workers were still logging into the SCADA network without the proper authentication policies. The attackers managed to infiltrate the network using Malware, gathered intelligence, and ultimately hijacked the VPN credentials to access the SCADA network that controlled the power grid.
This first-of-its-kind cyber attack shook the entire cybersecurity world. A combination of bad personnel cybersecurity training and lack of strong authentication policies led to half the homes, in a population of 1.4 million, without electricity for six hours.
Ensuring Cybersecurity in Electrical Substations
The Ukraine 2015 event unleashed new efforts to create regulations, methods, and cybersecurity measurements to prevent control networks like SCADA, from converging with IT.
But nowadays, the two IT and OT domains are slowly converging into one— IIoT domain. IIoT devices are making the lines between these two domains slowly disappear. IT pros are spending more time in the field— in the substation facilities, while OT personnel are starting to work on their networks and cybersecurity measures. Although the benefits of this convergence are exceptional, this also brings new challenging security flaws.
Cyberattacks to substations are generally targeted to operational control units like the Remote Terminal Unit (RTU) and the Intelligent Electronic Systems (IED), via the IT.
The following diagram shows the access to these components within a remote substation.
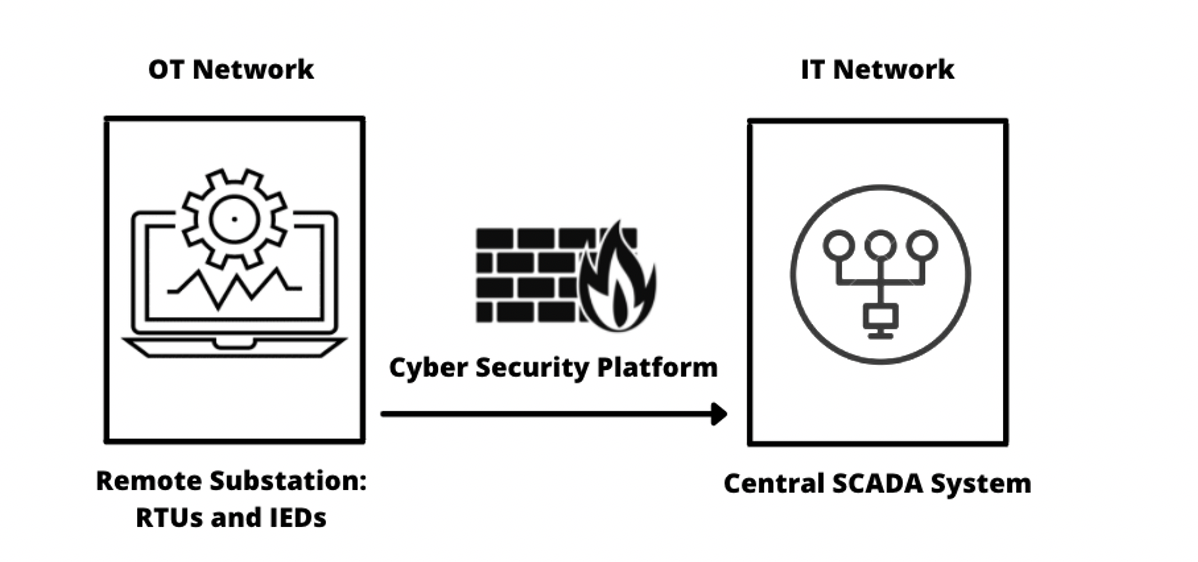
- Remote Substation controlled by Remote Terminal Units (RTUs) and Intelligent Electronic Devices (IEDs).
- ICS CyberSecurity Platform deployed in a substation. This unidirectional ICS gateway should protect communications between IT and OT domains.
- Central SCADA systems. The ICS Cybersecurity gateway protects WAN communications between remote (branch) RTUs and the central SCADA master system.
Unfortunately, OT control components such as RTUs, IDEs, within SCADA can’t be “air-gapped,” because that would inhibit operators from accessing remotely via SCADA WANs, so they must be at least properly segmented from IT domains.
What Does it Take to Properly Segment a Network?
A properly segmented network would require the right firewall rules, in addition to access control, authorization, and authentication policies, and the right router and switching configuration.
With cybersecurity platforms such as firewalls or IDS/IPS systems, the network segments and perimeters of electrical substations can be protected from external threats. But to be deployed in electrical substation environments, such electronic devices must be safe and compliant.
Any “IT” device, including a cybersecurity platform, should be capable of operating alongside the substation’s high-voltage equipment. In addition, it must also be capable of integrating with current management and monitoring systems like SCADA. And ultimately, it should protect the communications between sensitive OT equipment and IT, or IIoT with the Internet.
Segmenting IT and OT Domains with Purpose-Built Rugged Firewalls
Electrical substations face various environmental and service conditions that can be risky for unregulated electrical components. Electromagnetic Interference (EMI), radio interference, inductive load switching, electrostatic discharges, lightning strikes, and high current fault conditions, may interfere with any device.
Electronic devices, especially telecommunications appliances in electrical power substations need to be built with certain electrical immunity standards.
The IEC 61850-3/IEEE 1613 certified substation appliance.
The LEC-6041 is a wide temperature cyber-security appliance, designed to protect communications between IT and OT domains, and is suitable for substations. The LEC-6041 rugged ICS appliance is IEC-61850-3 and IEEE 1613 certified. Both certifications allow the device to communicate with other devices across electrical substations. The IEC-61850-3 standard defines communication protocols and networks for IEDs running at electrical substations. The implementations of IEC-61850 require that the Ethernet switches have the same ruggedness as the IEDs within the system.
In addition, the LEC-6041 is also IEEE 1613 certified. The IEEE 1613 is a standard for the environmental and testing requirements for IEDs installed in electric power substations. Other relevant certifications from rugged devices like LEC-6041 are CE/FCC Class A, IEC 61850-3, and IEEE 1613.
Other key components
Other key components that would make a traditional IT device suitable for operating under the substation’s conditions.
The Reverse Polarity Protection. This component ensures that a device is not damaged when the power supply’s polarity is reversed. With reverse polarity protection, the device is protected by cutting off the power going to the sensitive electronic circuits in the transmitter.
The Magnetic Isolation Protection. Magnetic isolation protection is also known as magnetic shielding, and it is a method for protecting sensitive electronic devices and data storage from magnetic fields. To reduce the effects of coupling from radio waves, voltage differences, and electrostatic and electromagnetic fields present in electrical substations, electrical devices must be shielded. For example, an 1.5 kV (kiloVolt) magnetic isolation protects the networking ports (Ethernet), and a 15 kV Electrostatic Discharge (ESD) can protect I/O ports, such as Serial or USB.






